The replace parameter specifies how exactly the configuration should be replaced:
- line – in this mode, only those commands that are not in the configuration are sent. This mode is used by default
- block – in this mode, all commands are sent if at least one command is missing
How to use replace: line parameter in module ios_config?
The replace: line mode is the default behavior. In this mode, if changes were detected, only the missing rows are sent.
For example, on a router such an ACL:
R1#sh run | s access
ip access-list extended IN_to_OUT
permit tcp 192.168.2.0 0.0.0.255 any eq www
permit tcp 192.168.2.0 0.0.0.255 any eq 22
permit icmp any anyLet’s try to run this playbook ios_config_replace_line.yml:
---
- name: Run cfg commands on router
hosts: 192.168.0.22
tasks:
- name: Config ACL
ios_config:
before:
- no ip access-list extended IN_to_OUT
parents:
- ip access-list extended IN_to_OUT
lines:
- permit tcp 192.168.2.0 0.0.0.255 any eq www
- permit tcp 192.168.2.0 0.0.0.255 any eq 22
- permit icmp any any
- deny ip any anyPlaybook execution:
$ ansible-playbook ios_config_replace_line.yml -v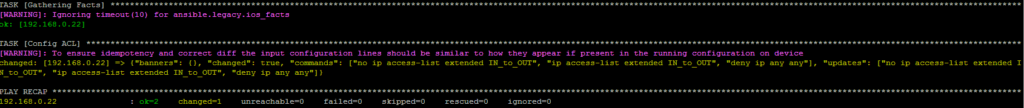
After that, on the router there is such an ACL:
R1#sh run | s access
ip access-list extended IN_to_OUT
deny ip any anyIn this case, the module checked which commands are missing in the ACL (since the default mode is match: line), found that the deny ip any any command was missing, and added it. But, since the ACL is first removed and then the list of lines commands is applied, it turned out that we now have an ACL with one line.
In such situations, the replace: block mode is appropriate.
How to use replace: line parameter in module ios_config?
In replace: block mode, all commands from the lines (and parents) list are sent if the device does not have at least one of these commands.
Let’s repeat the previous example.
ACL on the router:
R1#sh run | s access
ip access-list extended IN_to_OUT
permit tcp 10.0.1.0 0.0.0.255 any eq www
permit tcp 10.0.1.0 0.0.0.255 any eq 22
permit icmp any anyPlaybook execution:
$ ansible-playbook ios_config_replace_block.yml -v
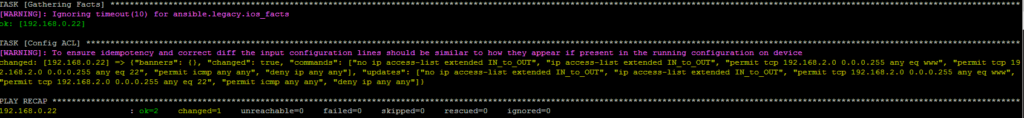
As a result, the ACL on the router is:
R1#sh run | s access
ip access-list extended IN_to_OUT
permit tcp 192.168.2.0 0.0.0.255 any eq www
permit tcp 192.168.2.0 0.0.0.255 any eq 22
permit icmp any any
deny ip any any